CompTIA SY0-601 Question Answer
A network analyst is investigating compromised corporate information. The analyst leads to a theory that network traffic was intercepted before being transmitted to the internet. The following output was captured on an internal host:
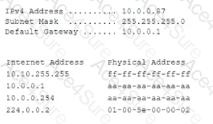
Based on the IoCS, which of the following was the MOST likely attack used to compromise the network communication?


