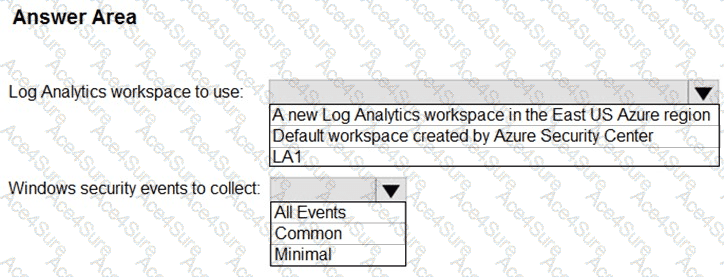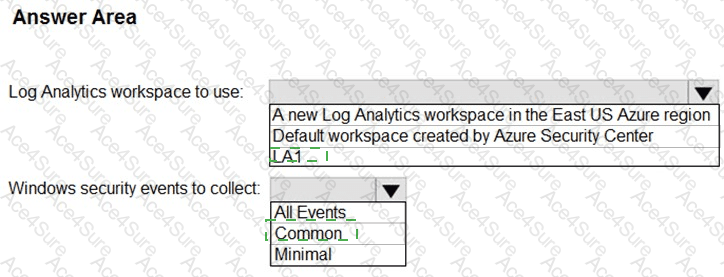
According to Microsoft Defender for Cloud (formerly Azure Security Center) documentation, when integrating servers and virtual machines for security monitoring, the Defender for Cloud data is stored and analyzed in a Log Analytics workspace. Microsoft best practices recommend using an existing workspace when one is already deployed for centralized log collection—especially if it already gathers telemetry from Azure and on-premises resources.
In this case, the existing workspace LA1 already “contains logs and metrics collected from all Azure resources and on-premises servers.” This satisfies the business requirement of “all servers must send logs to the same Log Analytics workspace.” Creating a new workspace would violate the cost-minimization and centralization requirements. Therefore, LA1 is the correct workspace to use.
For the Windows security events collection setting, Defender for Cloud offers three levels:
Common – collects a balanced set of security-related events (such as account logon, privilege use, and object access), recommended by Microsoft for most environments.
All Events – collects every possible security event, which increases data ingestion cost and is typically used only for high-security or regulated environments.
Because Litware Inc. must minimize cost while ensuring a full audit trail of user activities, the Common level provides the optimal balance of visibility and cost efficiency.
Therefore, based on Microsoft Defender for Cloud configuration guidelines:
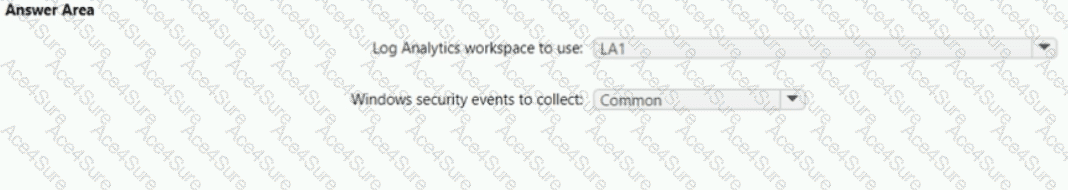
✅ Log Analytics workspace to use: LA1
✅ Windows security events to collect: Common