In Microsoft Sentinel, the Advanced Security Information Model (ASIM) provides a standardized schema and parser layer for common telemetry types (DNS, Authentication, NetworkSession, etc.). To investigate DNS-related activity, you should use the ASIM-normalized table ASim_Dns, which unifies data from multiple DNS sources (Microsoft Defender for Endpoint, Azure Firewall, DNS servers, etc.) under a consistent schema.
The ASim_Dns parser standardizes key fields such as:
ResponseCodeName → name of the DNS response code (e.g., NXDOMAIN, NOERROR, etc.)
QueryName → domain name queried
SrcIpAddr and DstIpAddr → IP addresses involved
To investigate recent DNS failures (e.g., non-existent domains), the query filters for events where:
ResponseCodeName == "NXDOMAIN" — identifies DNS lookups that returned “Non-Existent Domain,” a common indicator of suspicious or misconfigured activity.
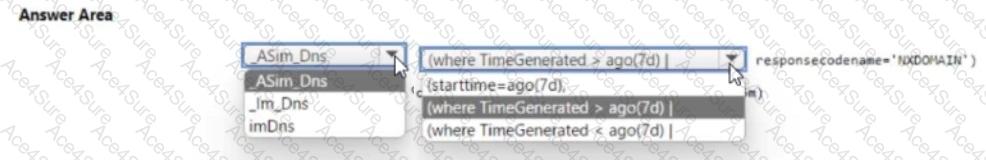
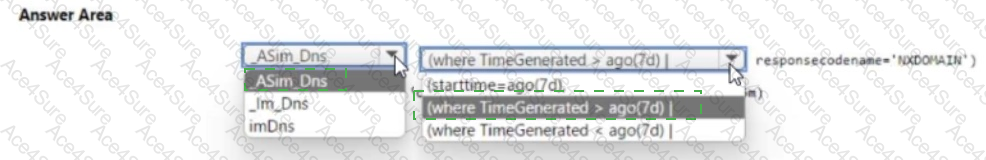
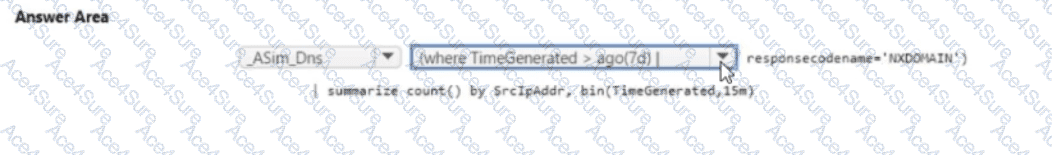
Therefore, the correct and compliant ASIM-based query syntax is:
ASim_Dns
| where TimeGenerated > ago(7d)
| where ResponseCodeName == "NXDOMAIN"
This approach ensures your investigation leverages ASIM normalization and aligns with Microsoft Sentinel best practices for DNS event analysis.