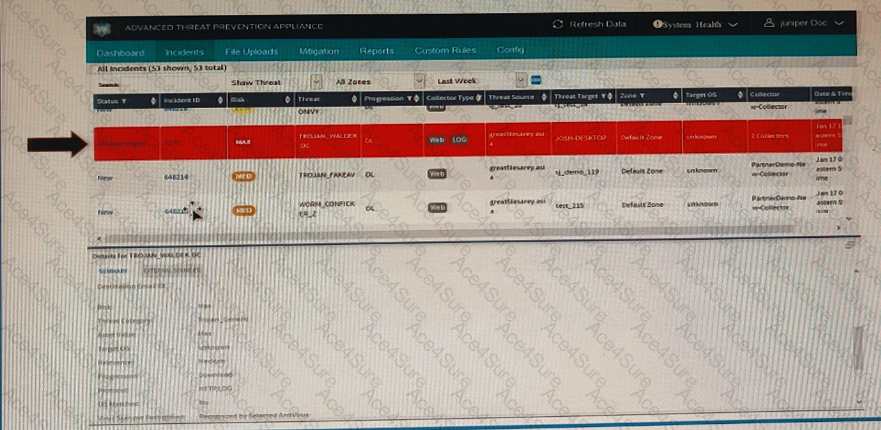
The appropriate mitigation actions for the selected incident are to block malware IP addresses (download server or CnC server) and to deploy IVP integration (if configured) to confirm if the endpoint has executed the malware and is infected. This is because the incident shows a progression level of “Download” in the kill chain, which means that the malware has been downloaded and is likely to be executed. Blocking the malware IP addresses can prevent further communication with the malicious server and stop the malware from receiving commands or exfiltrating data. Deploying IVP integration can help verify the infection status of the endpoint and provide additional information about the malware behavior and impact. IVP integration is an optional feature that allows the ATP Appliance to interact with third-party endpoint security solutions such as Carbon Black, Cylance, and CrowdStrike. References:
Advanced Threat Prevention Appliance Solution Brief
Advanced Threat Prevention Appliance Datasheet
[Advanced Threat Prevention Appliance Mitigation Actions]
[Advanced Threat Prevention Appliance IVP Integration]