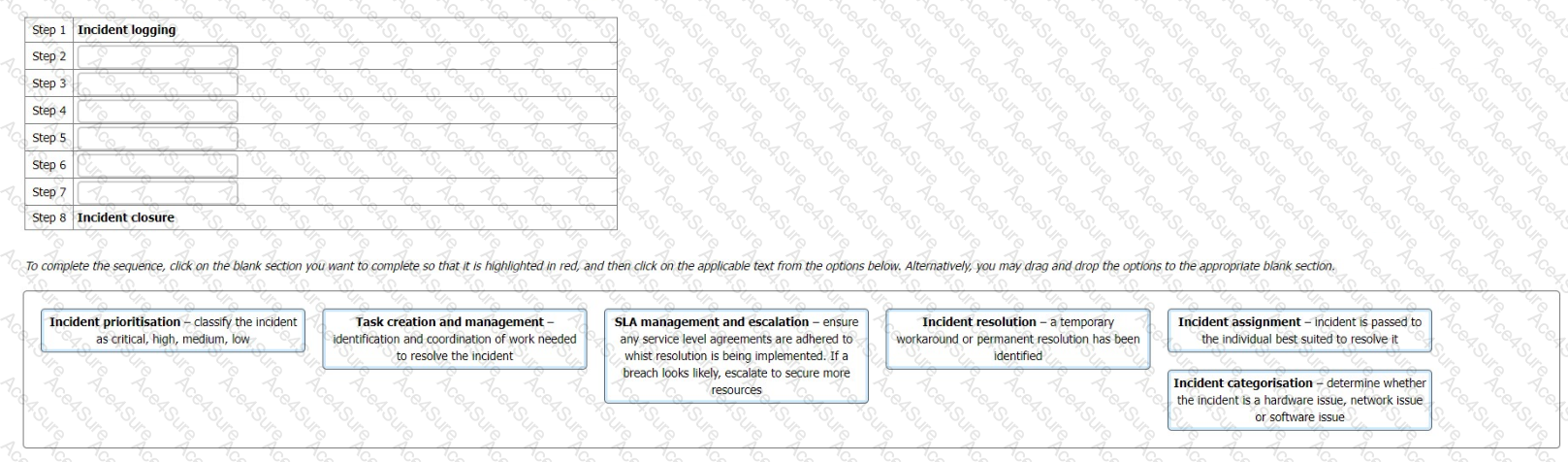
Step 1 = Incident logging Step 2 = Incident categorisation Step 3 = Incident prioritisation Step 4 = Incident assignment Step 5 = Task creation and management Step 6 = SLA management and escalation Step 7 = Incident resolution Step 8 = Incident closure
The order of the stages in the information security incident management process should follow a logical sequence that ensures a quick, effective, and orderly response to the incidents, events, and weaknesses. The order should also be consistent with the best practices and guidance provided by ISO/IEC 27001:2022 and ISO/IEC 27035:2022. Therefore, the following order is suggested:
Step 1 = Incident logging: This step involves recording the details of the potential incident, event, or weakness, such as the date, time, source, description, impact, and reporter. This step is important to provide a traceable record of the incident and to facilitate the subsequent analysis and response. This step is related to control A.16.1.1 of ISO/IEC 27001:2022, which requires the organization to establish responsibilities and procedures for the management of information security incidents, events, and weaknesses. This step is also related to clause 6.2 of ISO/IEC 27035:2022, which provides guidance on how to log the incidents, events, and weaknesses.
Step 2 = Incident categorisation: This step involves determining the type and nature of the incident, event, or weakness, such as whether it is a hardware issue, network issue, or software issue. This step is important to classify the incident and to assign it to the appropriate resolver or team. This step is related to control A.16.1.2 of ISO/IEC 27001:2022, which requires the organization to report information security events and weaknesses as quickly as possible through appropriate management channels. This step is also related to clause 6.3 of ISO/IEC 27035:2022, which provides guidance on how to categorize the incidents, events, and weaknesses.
Step 3 = Incident prioritisation: This step involves assessing the severity and urgency of the incident, event, or weakness, and classifying it as critical, high, medium, or low. This step is important to prioritize the incident and to allocate the necessary resources and time for the response. This step is related to control A.16.1.3 of ISO/IEC 27001:2022, which requires the organization to assess and prioritize information security events and weaknesses in accordance with the defined criteria. This step is also related to clause 6.4 of ISO/IEC 27035:2022, which provides guidance on how to prioritize the incidents, events, and weaknesses.
Step 4 = Incident assignment: This step involves passing the incident, event, or weakness to the individual or team who is best suited to resolve it, based on their skills, knowledge, and availability. This step is important to ensure that the incident is handled by the right person or team and to avoid delays or confusion. This step is related to control A.16.1.4 of ISO/IEC 27001:2022, which requires the organization to respond to information security events and weaknesses in a timely manner, according to the agreed procedures. This step is also related to clause 6.5 of ISO/IEC 27035:2022, which provides guidance on how to assign the incidents, events, and weaknesses.
Step 5 = Task creation and management: This step involves identifying and coordinating the work needed to resolve the incident, event, or weakness, such as performing root cause analysis, testing solutions, implementing changes, and documenting actions. This step is important to ensure that the incident is resolved effectively and efficiently, and that the actions are tracked and controlled. This step is related to control A.16.1.5 of ISO/IEC 27001:2022, which requires the organization to apply lessons learned from information security events and weaknesses to take corrective and preventive actions. This step is also related to clause 6.6 of ISO/IEC 27035:2022, which provides guidance on how to create and manage the tasks for the incidents, events, and weaknesses.
Step 6 = SLA management and escalation: This step involves ensuring that any service level agreements (SLAs) are adhered to while the resolution is being implemented, and that the incident is escalated to a higher level of authority or support if a breach looks likely or occurs. This step is important to ensure that the incident is resolved within the agreed time frame and quality, and that any deviations or issues are communicated and addressed. This step is related to control A.16.1.6 of ISO/IEC 27001:2022, which requires the organization to communicate information security events and weaknesses to the relevant internal and external parties, as appropriate. This step is also related to clause 6.7 of ISO/IEC 27035:2022, which provides guidance on how to manage the SLAs and escalations for the incidents, events, and weaknesses.
Step 7 = Incident resolution: This step involves applying a temporary workaround or a permanent solution to resolve the incident, event, or weakness, and restoring the normal operation of the information and information processing facilities. This step is important to ensure that the incident is resolved completely and satisfactorily, and that the information security is restored to the desired level. This step is related to control A.16.1.7 of ISO/IEC 27001:2022, which requires the organization to identify the cause of information security events and weaknesses, and to take actions to prevent their recurrence or occurrence. This step is also related to clause 6.8 of ISO/IEC 27035:2022, which provides guidance on how to resolve the incidents, events, and weaknesses.
Step 8 = Incident closure: This step involves closing the incident, event, or weakness, after verifying that it has been resolved satisfactorily, and that all the actions have been completed and documented. This step is important to ensure that the incident is formally closed and that no further actions are required. This step is related to control A.16.1.8 of ISO/IEC 27001:2022, which requires the organization to collect evidence and document the information security events and weaknesses, and the actions taken. This step is also related to clause 6.9 of ISO/IEC 27035:2022, which provides guidance on how to close the incidents, events, and weaknesses.