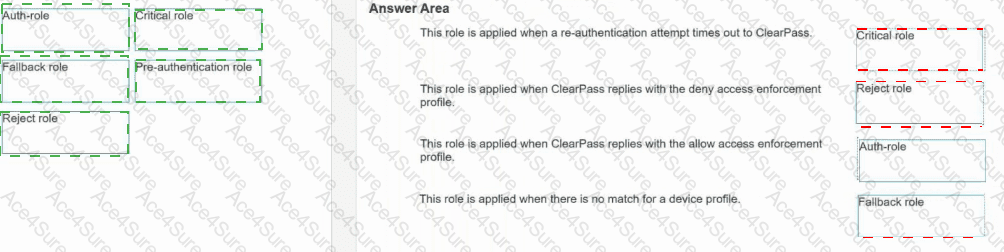
Scenario
Correct Role
This role is applied when a re-authentication attempt times out to ClearPass.
Critical role
This role is applied when ClearPass replies with the deny access enforcement profile.
Reject role
This role is applied when ClearPass replies with the allow access enforcement profile.
Auth-role
This role is applied when there is no match for a device profile.
Fallback role
In Aruba CX switching, when integrating ClearPass Policy Manager (CPPM) for 802.1X, MAC Authentication, or Downloadable Role-based Access, the system assigns specific roles based on AAA enforcement outcomes or network events (timeouts, mismatches, or unknown devices).
These special roles ensure network survivability and consistent zero-trust policy enforcement even if ClearPass or RADIUS communication fails.
1. Critical Role → Applied when re-authentication attempt times out to ClearPass
“When the switch cannot reach the RADIUS server during re-authentication (for example, a timeout), the switch assigns the critical-role to the authenticated client, ensuring continued network connectivity with a restricted policy.”
“This role is used to maintain limited access when the RADIUS server is unreachable or times out.”
This ensures that devices remain minimally operational while preventing full network access — crucial for survivable network designs.
2. Reject Role → Applied when ClearPass replies with the deny access enforcement profile
“If the RADIUS response includes an Access-Reject, the switch applies the configured reject-role. This typically results in isolation or complete denial of access.”
“The reject-role allows enforcement of a restrictive VLAN or ACL after authentication failure.”
Therefore, when ClearPass denies access, the reject role provides an explicit enforcement action.
3. Auth-Role → Applied when ClearPass replies with the allow access enforcement profile
“When the authentication succeeds and the RADIUS server returns an Access-Accept with an Aruba-User-Role attribute, the switch applies the auth-role.”
“This is the default operational role for authenticated clients.”
This role represents the authorized state, where the user receives full or role-based access according to ClearPass policies.
4. Fallback Role → Applied when there is no match for a device profile
“If the client fails device profiling or no match is found in the endpoint database, the switch applies the fallback-role configured for unknown devices.”
“The fallback-role provides a baseline policy for unrecognized or unclassified endpoints.”
This ensures unknown or new devices can be placed in a limited-access posture pending classification.
References of HPE Aruba Networking Switching Documents or Study Guide:
ArubaOS-CX Access Security Guide (AOS-CX 10.12 and later) – “Role mapping and special roles (auth-role, reject-role, fallback-role, critical-role).”
Aruba ClearPass Policy Manager Deployment Guide – “Integration with Aruba Switch Roles and Enforcement Profile Mapping.”
Aruba Zero Trust Wired Access Design Guide – “Survivability roles for authentication failure or unreachable ClearPass.”
Aruba CX 6300 Configuration Guide – “AAA, Downloadable Roles, and Fallback/Critical Role Configuration.”