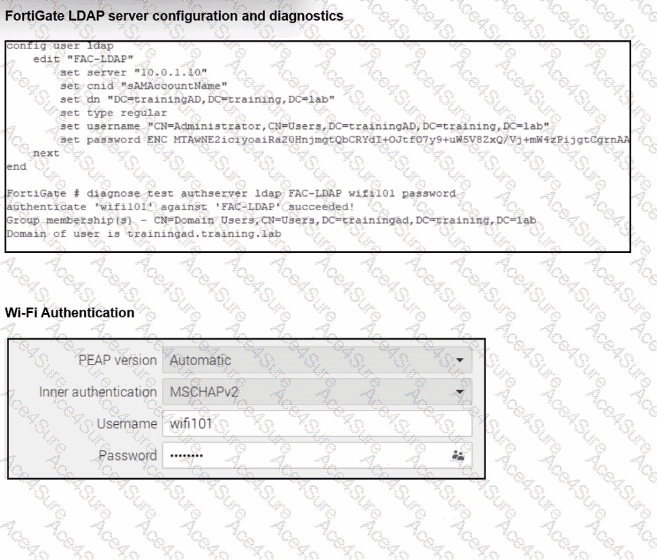
From the exhibit, LDAP on FortiGate is correctly configured and tested:
diagnose test authserver ldap FAC-LDAP wifi101 password
authenticate 'wifi101' against 'FAC-LDAP' succeeded!
Group membership(s) - CN=Domain Users,...
So:
LDAP connectivity works
Bind DN, DN, CNID, and credentials are correct(so optionCis eliminated).
Firewall policies do not affect the802.1X / Wi-Fi authentication stepitself, soAis not the root cause.
Nothing in the scenario indicates that AD is enforcing LDAPS-only; the LDAP test already succeeds using the configured parameters, soBis also excluded.
The Wi-Fi supplicant is configured forPEAP with inner authentication = MSCHAPv2.
MSCHAPv2 is achallenge–response mechanism designed for RADIUS, not for LDAP simple bind. FortiGate’s LDAP implementation uses asimple bind (username/password) over LDAP or LDAPS, and it doesnotimplement MSCHAPv2 against LDAP backends.
In Fortinet’s design, if you needPEAP-MSCHAPv2 with Active Directory, you must use:
ARADIUS server(such as Windows NPS or FortiAuthenticator), and
Have FortiGate use RADIUS,notLDAP, as the authentication backend for 802.1X / Wi-Fi users.
Because FortiGate cannot process MSCHAPv2 exchanges directly against an LDAP server, authentication fails when the inner method is MSCHAPv2, even though LDAP works when tested with a simple bind from the CLI.