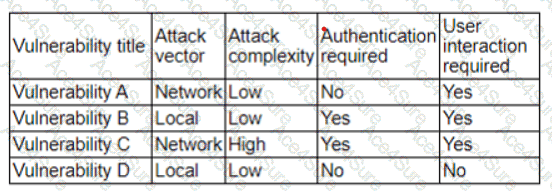
To determine the correct vulnerability, you must map the specific threat intelligence (users clicking email links) to the CVSS Base Metrics provided in the table.
1. Analyze the Scenario:
Threat Vector: "End users frequently click on malicious links sent via email."
Attack Vector implication: The attack is coming from outside the organization (remote), meaning the Attack Vector must be Network.
Interaction implication: The success of the attack relies on the user performing an action (clicking), meaning User Interaction must be Yes (Required).
2. Evaluate the Table:
Vulnerability
Attack Vector
Attack Complexity
Auth Required
User Interaction
Analysis
A
Network
Low
No
Yes
Perfect Match. This represents a remote exploit (e.g., a browser drive-by download or malicious site) that triggers when a user clicks a link. It requires no authentication and is easy to execute.
B
Local
Low
Yes
Yes
Incorrect. "Local" usually implies the attacker already has physical access or a foothold. "Auth Required" makes it harder to exploit than A.
C
Network
High
Yes
Yes
Incorrect. "High" complexity and "Auth Required" make this significantly less likely/severe than A for a mass phishing campaign.
D
Local
Low
No
No
Incorrect. "Local" vector and "User Interaction: No" do not align with the specific threat of users clicking links.
3. Conclusion:
Vulnerability A is the highest risk because it is Remotely Exploitable (Network), easy to perform (Complexity: Low), requires No Authentication (anyone who clicks is vulnerable), and directly targets the behavior identified in the threat intelligence (User Interaction: Yes).
Attack Vector (AV:N): The context of "email" typically maps to Network because the payload is delivered over the internet/network stack.
User Interaction (UI:R): CompTIA defines this metric as required when a user must perform an action (like clicking a link or opening an attachment) for the vulnerability to be successfully exploited.
Risk Prioritization: Vulnerabilities with Network vectors and Low complexity are generally prioritized over Local/High Complexity ones because they are easier to scale and automate.