CompTIA CS0-002 Question Answer
A security analyst reviews the following post-incident information to determine the origin and cause of a breach:
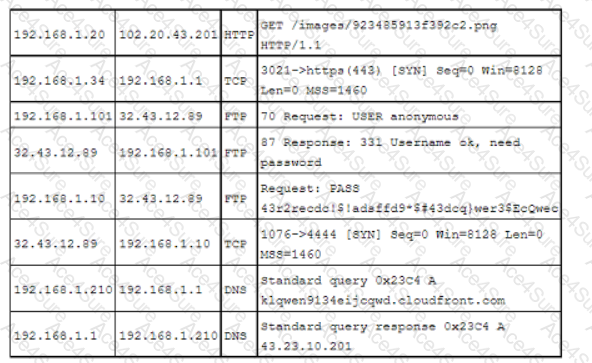
Based on this information, which of the following should the analyst record in the incident report related to the breach? (Select two).


