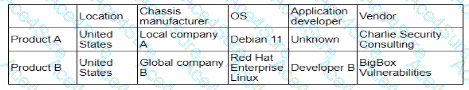
The table shows detailed information about products, includinglocation, chassis manufacturer, OS, application developer, and vendor. This type of information is typically assessed in a supply chain assessment to evaluate the security and reliability of components and services from different suppliers.
Why Supply Chain Assessment?
Component Evaluation: Assessing the origin and security of each component used in the products, including hardware, software, and third-party services.
Vendor Reliability: Evaluating the security practices and reliability of vendors involved in providing components or services.
Risk Management: Identifying potential risks associated with the supply chain, such as vulnerabilities in third-party components or insecure development practices.
Other types of assessments do not align with the detailed supplier and component information provided:
A. System: Focuses on individual system security, not the broader supply chain.
C. Quantitative: Focuses on numerical risk assessments, not supplier information.
D. Organizational: Focuses on internal organizational practices, not external suppliers.
[References:, CompTIA SecurityX Study Guide, NIST Special Publication 800-161, "Supply Chain Risk Management Practices for Federal Information Systems and Organizations", "Supply Chain Security Best Practices," Gartner Research, , , , ]