CompTIA CAS-005 Question Answer
A security analyst is reviewingsuspicious log-in activity and sees the following data in the SICM:
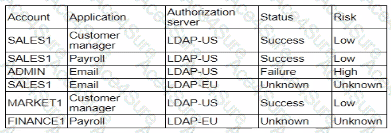
Which of the following is the most appropriate action for the analyst to take?
CompTIA CAS-005 Question Answer
A security analyst is reviewingsuspicious log-in activity and sees the following data in the SICM:

Which of the following is the most appropriate action for the analyst to take?