Cisco 350-901 Question Answer
Refer to the exhibit.
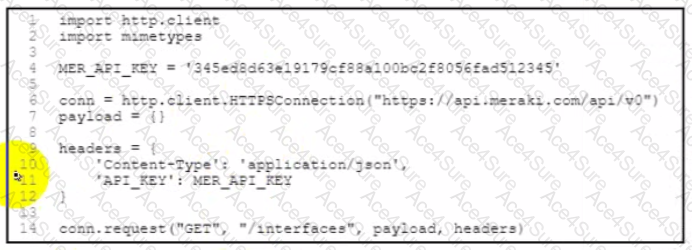
A developer created a Python script to retrieve interface information for the devices in a MeraKi network environment. A security analyst has reviewed the code and observed poor secret storage practices. What is the appropriate password storage approach?


