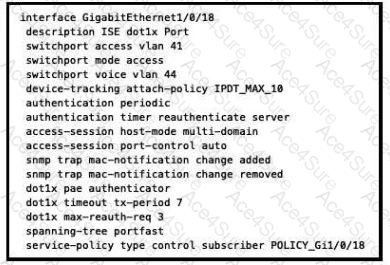
Based on the configuration script in the image, the interface GigabitEthernet0/0/18 is configured for both 802.1X and MAB authentication. The command authentication port-control auto enables 802.1X authentication on the port, while the command dot1x pae authenticator enables the port to act as an authenticator. The command authentication host-mode multi-domain enables MAB authentication on the port, and allows two devices to be authenticated, one in the voice VLAN and one in the data VLAN. Therefore, when a device tries to connect to the port, the switch will first attempt 802.1X authentication, and if it fails, it will fall back to MAB authentication using the device’s MAC address. The switch will then contact the ISE server, which is configured as the RADIUS server group ise-group, to verify the device’s credentials and assign the appropriate access level based on the ISE policy. The ISE policy can also dynamically assign VLANs, ACLs, or service policies to the device based on its identity and posture. References :=
Some possible references are:
[Implementing and Operating Cisco Security Core Technologies (SCOR) v1.0], Module 6: Secure Connectivity, Lesson 6.2: Implementing Site-to-Site VPNs, Topic 6.2.2: Group Encrypted Transport VPN
Cisco IOS Security Configuration Guide, Release 15M&T - Configuring IEEE 802.1x Port-Based Authentication
Cisco IOS Security Configuration Guide, Release 15M&T - Configuring MAC Authentication Bypass
Cisco Identity Services Engine Administrator Guide, Release 2.7 - Configure Wired 802.1X and MAB