Cisco 350-201 Question Answer
Refer to the exhibit.
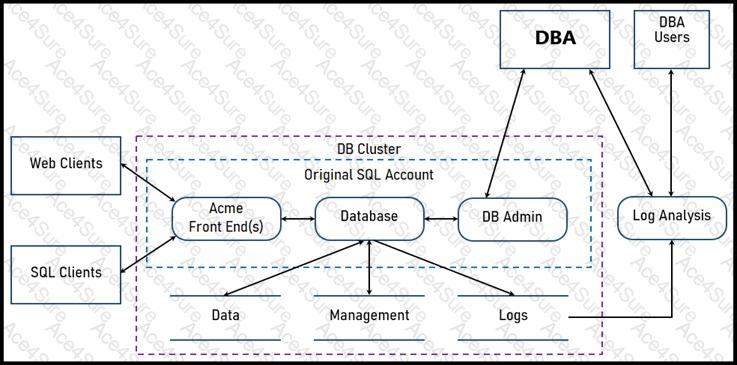
Two types of clients are accessing the front ends and the core database that manages transactions, access control, and atomicity. What is the threat model for the SQL database?
Previous
Cisco 350-201 Question Answer
Refer to the exhibit.

Two types of clients are accessing the front ends and the core database that manages transactions, access control, and atomicity. What is the threat model for the SQL database?