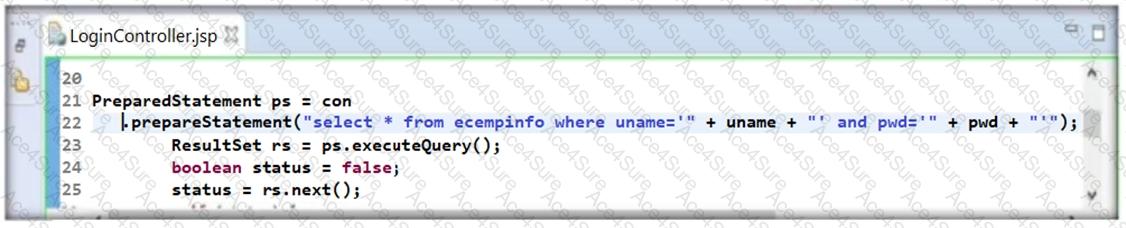
The code snippet provided in the image is a Java program where a SQL query is being constructed by concatenating user inputs directly into the query string. This practice is highly insecure as it opens up the application to SQL Injection attacks. In this specific example, uname and pwd are directly appended to the SQL query string without any sanitization or parameterization, making it vulnerable.
A secure practice would be to use parameterized queries or prepared statements which ensure that user inputs are treated as data and not executable code. This prevents malicious users from injecting harmful SQL code into the application.
Here’s how the corrected code using parameterized queries should look:
Java
PreparedStatement ps = con.prepareStatement("SELECT * FROM empinfo WHERE uname=? AND pwd=?");
ps.setString(1, uname);
ps.setString(2, pwd);
ResultSet rs = ps.executeQuery();
AI-generated code. Review and use carefully. More info on FAQ.
In this corrected version, ? placeholders are used in the SQL query string for user inputs, and then those placeholders are replaced with actual user input values using setString() method calls on the PreparedStatement object. This ensures that user inputs are safely incorporated into the SQL query, preventing SQL Injection.
References:
EC-Council Application Security Engineer (CASE) JAVA official study guides and materials emphasize on secure coding practices including avoiding non-parameterized queries to prevent security vulnerabilities like SQL Injection.
Specific topics covering secure coding practices in Java can be found in modules focusing on data validation and sanitization.