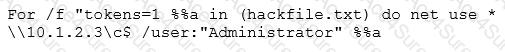
The command shown is a Windows batch loop that attempts to mount a hidden administrative share (c$) on a remote machine (\10.1.2.3) using the username "Administrator" and a list of passwords from the file hackfile.txt.
for /f "tokens=1 %%a in (hackfile.txt) → Reads one password per line from the file
do net use * \10.1.2.3\c$ /user:"Administrator" %%a → Tries to authenticate to the share using the Administrator account and each password
This is a classic brute-force password attack attempting to crack the Administrator account using a wordlist.
From CEH v13 Official Courseware:
Module 4: Enumeration
Module 6: Malware and Password Cracking Techniques
CEH v13 Study Guide states:
“Tools and scripts that automate login attempts using SMB shares and administrative credentials can be used to brute force user accounts. An attacker attempts access using a list of passwords (dictionary attack).”
Incorrect Options:
A: The connection attempt is made, but the success is dependent on password cracking.
B: This command does not enumerate users.
D: No null session involved; this is a brute-force attempt, not privilege escalation.
[Reference:CEH v13 Study Guide – Module 4: Enumeration → Brute-force TechniquesMicrosoft TechNet: net use command documentation, ==================================================================, , ]
 What is Eve trying to do?
What is Eve trying to do?

