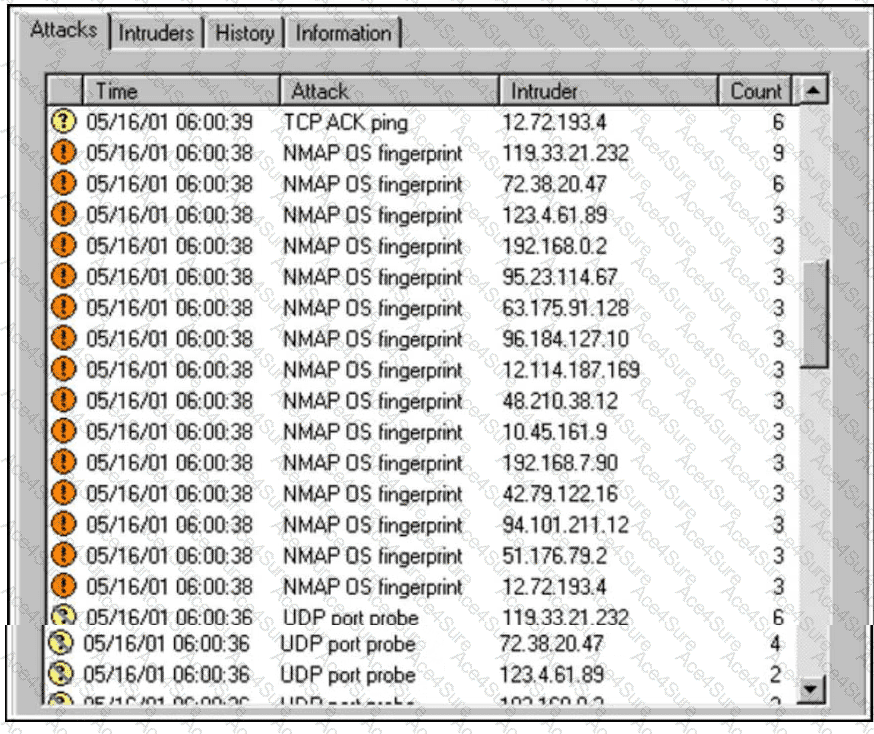
The correct answer isNetwork/host artifacts. To understand why, it is important to map the observed attacker behavior to thePyramid of Pain, a model that ranks indicators by how difficult they are for adversaries to change once detected.
In this scenario, the adversary is usingNmap OS fingerprinting, which involves sending carefully crafted packets and analyzing responses (TCP/IP stack behavior, TTL values, window sizes, flags, and timing characteristics). These behaviors leave behindnetwork and host artifacts, such as distinctive scan patterns, abnormal TCP flag combinations, OS fingerprinting probes, and consistent tool-specific traffic signatures.
On the Pyramid of Pain:
IP addresses (D)sit at the very bottom. Attackers can trivially change IPs using VPNs, proxies, or botnets.
Port probes (B)andUDPs (A)represent low-level indicators that are also easy to modify. An attacker can change scan ports, protocols, or scan timing with minimal effort.
Network/host artifacts (C)sit significantly higher. These include tool-generated behaviors, protocol anomalies, OS fingerprinting patterns, and scan logic inherent to tools like Nmap. Changing these requires attackers to reconfigure tools, write custom scanners, or significantly alter their operational approach.
From a threat hunting and SOC maturity perspective, detecting and alerting onnetwork and host artifactsforces attackers to expend more time and resources, increasing their operational cost. This aligns with the core objective of the Pyramid of Pain:maximize adversary pain by detecting behaviors, not easily replaceable indicators.
Professionally mature SOC teams focus on identifying scanning techniques (e.g., Nmap OS detection, TCP ACK probes, UDP probes) rather than blocking individual IPs. These detections are resilient, scalable, and effective against both commodity attackers and advanced adversaries.
In short, while IPs and ports are useful for short-term containment,network and host artifacts provide the highest-value indicators in this scenario, makingCthe correct answer.