Cisco 300-215 Question Answer
Refer to the exhibit.
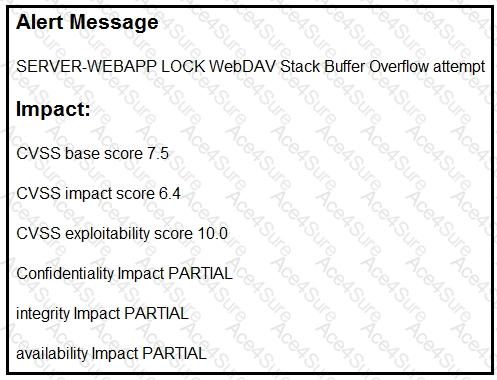
After a cyber attack, an engineer is analyzing an alert that was missed on the intrusion detection system. The attack exploited a vulnerability in a business-critical, web-based application and violated its availability. Which two mitigation techniques should the engineer recommend? (Choose two.)


