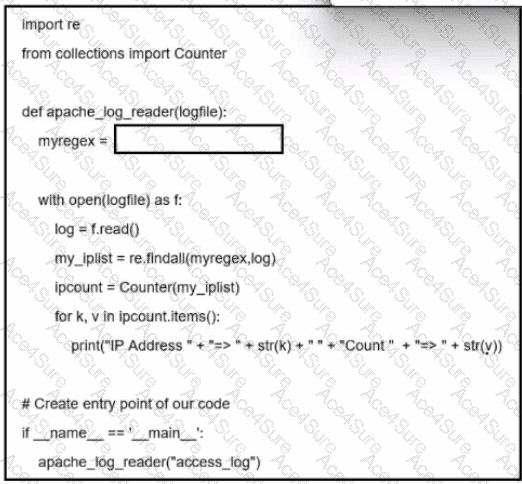
The goal of the given Python code is to parse an Apache access log and extract IP addresses using regular expressions (regex). In this context, the most appropriate regex pattern to extract IPv4 addresses from log data is:
r'\d{1,3}.\d{1,3}.\d{1,3}.\d{1,3}'
This pattern matches typical IPv4 addresses, where each octet consists of 1 to 3 digits separated by periods. For example, it matches addresses like192.168.1.1or10.0.0.123. The pattern uses:
\d{1,3}to capture between 1 and 3 digits,
\.to match the dot (escaped since.is a special character in regex),
repeated 4 times with proper separation to form the full IPv4 structure.
Options A, B, and C either include incorrect syntax, improper escape sequences, or do not represent a valid IP address pattern.
This type of log analysis and pattern extraction is described in the Cisco CyberOps Associate curriculum under basic scripting and automation techniques used in log and artifact analysis.
[Reference:CyberOps Technologies (CBRFIR) 300-215 study guide, Section: “Basic Python Scripting for Security Analysts” and “Log Analysis and Data Extraction using Regex.”]