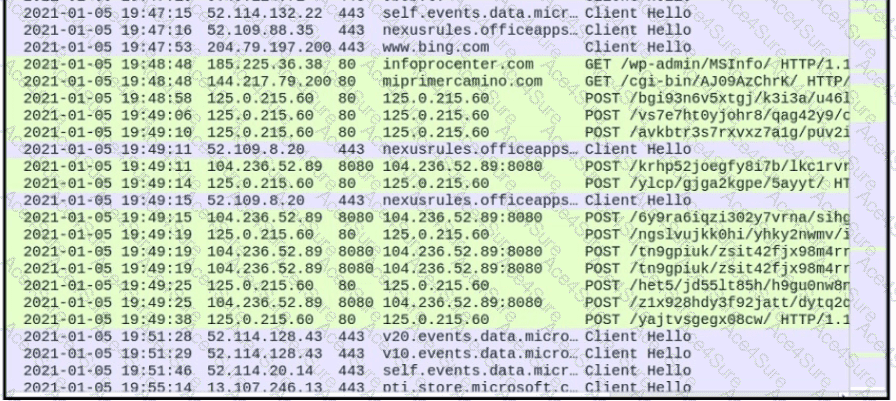
A.
Identifying possible malware communications and botnet activity
B.
Monitoring of encrypted and unencrypted web sessions for diagnostics.
C.
Analysis of traffic flows during network capacity testing
D.
Review of session logs for performance optimization in a distributed application environment