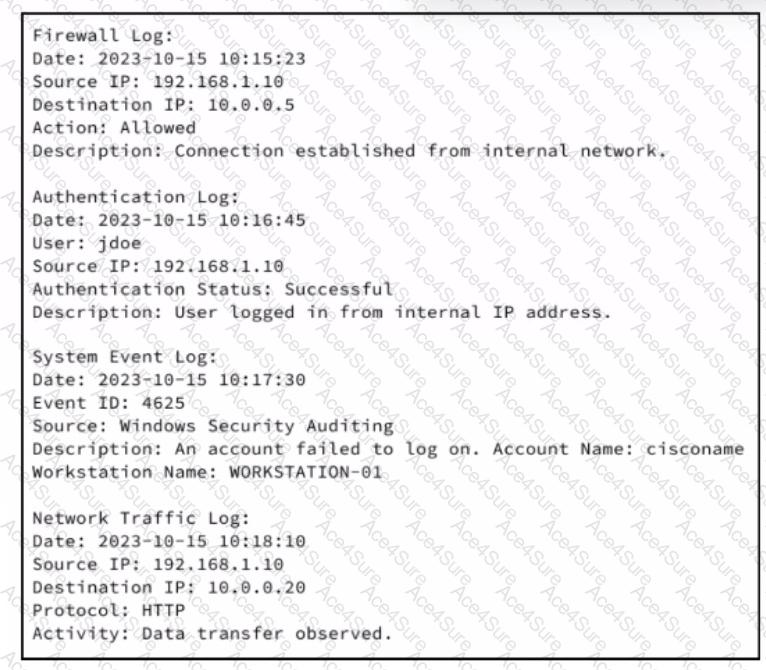
In cybersecurity operations, evidence classification is critical for incident investigation and validation. An Intrusion Detection System (IDS) alert serves as the initial indicator of suspicious activity, such as potential data exfiltration. However, IDS alerts alone are often insufficient to confirm malicious behavior, as they may produce false positives or incomplete context.
The additional logs collected—such as firewall logs, authentication logs, system event logs, and network traffic logs—are used to support, validate, and confirm the original alert. These logs show related activity from the same source IP, including successful authentication, failed login attempts, and observed data transfers over HTTP. When multiple independent data sources align with the original IDS alert, they strengthen the confidence that the activity is real and malicious.
This type of supporting information is known as corroborative evidence. Corroborative evidence does not stand alone as the initial detection but reinforces the validity of primary evidence by confirming the same behavior across different systems and logs. Cybersecurity operations documentation emphasizes log correlation as a foundational SOC function precisely for this reason.
Primary evidence would be the original IDS alert itself, as it directly detected the suspicious activity. Circumstantial evidence implies indirect inference without direct linkage, which is not the case here because the logs clearly relate to the same host and timeline. Secondary evidence typically refers to derivative or summarized data rather than direct system-generated records.
By correlating IDS alerts with firewall, authentication, and network logs, analysts build a reliable incident narrative and reduce false positives. Therefore, the logs collected provide corroborative evidence, making Option A the correct answer.